Aspects of ITOM and ITSM in Public Sector Organizations
Need for highly complex decisions give rise to highly complex challenges.
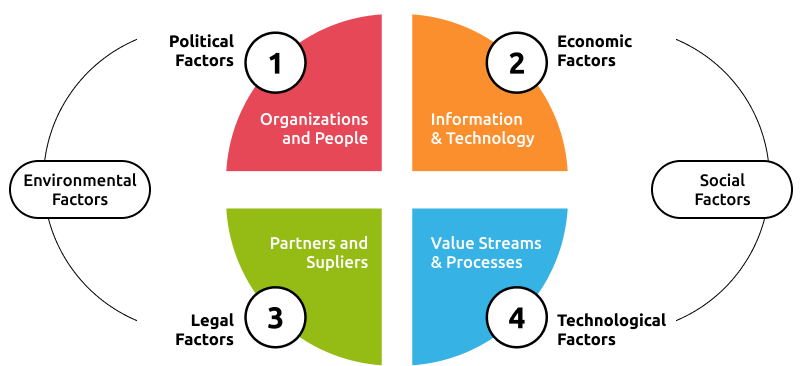
Today's top challenges for a public sector CIO
Services tailored for our public sector partners
Technology
Advisory
PITG provides expert guidance supported by top-tier knowledge and in sync with the ebb and flow of technological developments to Create an effective IT Strategy.

Designing and Solution Architecting
We design, build, & deploy software solutions customised for big scale PSU’s business specific needs, to help them avoid the common and sometimes unpredictable pitfalls that proper solution design can mitigate.

Accelerated Implementation
PITG offers accelerated and secure implementation in client’s agile environment, that systematically analyses and generates tactics to manage the human elements critical to successful implementation.

Custom Development & Integration
We provide best in class services which streamlines the work processes, simplifies data input, and performs high-speed analysis, and produces actionable insight meeting client's critical requirements.

Compliance & Audits
PITG's value addition in implementations also entails its robust audit capabilities, spanning all the prevalent standards, including: ISO 27001, NIST CSF, COBIT, PCIDSS, HIPAA, GDPR, SOC & COSO.

Continuous Upgrades to stay ahead of Attackers
We provide proactive defence solutions & strategic implementation, that reduces chances of malicious attacks staying ahead of the curve ensuring client’s data security by identifying, assessing, and correcting vulnerabilities in software applications before the software is integrated.
It is critical for us to adhere to compliance frameworks

ISO 270001

SOC

GDPR

HIPPA

PCI-EDSS

NIST CSF

COBIT
Case Studies

Establishment of a coherent monitoring system
A government department responsible for regulating the functions of corporate entities found it essential to detect and scrutinize all the configurable items (CIs) within a specific geographical boundary. The likelihood of inadvertently overlooking precise critical information by human operators, made it more challenging in ensuring proactive monitoring and control within the given environment. PITG provided a solution which was an orchestration of diverse tools used to convert all transactions, from being unmonitored with lack of vigilance, towards being consistently monitored and reported.

Intranet implementation of Identity Manager and Access Manager
The largest defence equipment manufacturer of India, headquartered in Kolkata found it challenging to maintain extremely high level of security and meet compliance requirements. They needed to ensure that each of its employees can only access the systems relevant to their specific roles. PITG’s role was to implement Identity and access manager which significantly reduced the risk of highly confidential data being breached.

Strategic implementation of Identity Manager and Access Manager
Indian nationalised bank under the ownership of Ministry of Finance, required a strategic technology plan to implement new systems over the period as a result of the growth of new banking products. PITG’'s task was to implement a full IDAM stack across their entire organisation, hoping to boost productivity— while untethering employees from a traditional office setting. Successful implementation of the solutions improved security, access governance and reduced dependency.

Many to one mapping of identities
An Indian government-owned mining and refining corporation, headquartered in Kolkata wanted to implement a full identity and access management stack across their entire organization, hoping to boost productivity— while untethering employees from a traditional office setting.. Being a public sector undertaking (PSU), and the seventh largest employer in India with nearly 272,000 employees, their challenge was to manage identities of all their users and grant them role and policy-based access to internal resources.